This blog post is written in English, as it originates from an English request in Microsoft’s Q&A page: https://docs.microsoft.com/en-us/answers/questions/661335/intune-bitlocker-key-after-deletion-of-device.html.
A short introduction, how it came to this request.
In a normal Windows installation you cannot access the data of another user, because the permissions on files are regulated in the file system NTFS. However, if you access the files on the hard disk from another operating system (e.g. started from a USB stick), you can access all files.
When a device is taken out of service, the hard disk must be completely erased for security reason. For this purpose, it is overwritten one or more times with other data or zeros, this is called „wipe a disk“.
If a hard disk is encrypted, it is not possible to access the data from another operating system. It is therefore no longer necessary to wipe the hard disk – without the key, no one can view the encrypted files.
We have been encrypting our devices with BitLocker for some time, managed with Intune and Azure AD. So all’s well? Not quite. The original BitLocker encrypted disk „loses“ its encryption after you delete the device from Intune and Azure AD. So now someone could boot the device from a USB stick and sees all data stored on the disk.
This test was made with a hybrid joined device.
First I checked if the hard disk was really encrypted. In the screenshot you can see that the encryption of C: is enabled.
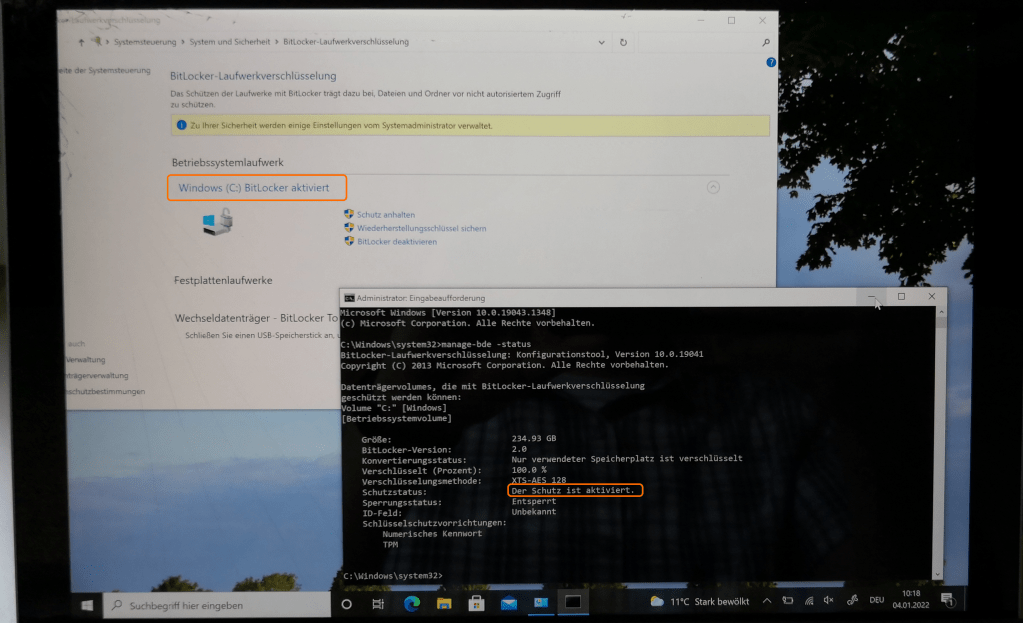
If you boot another operating system from a USB stick (here a Windows based on Win PE), you cannot access the contents of the hard disk. You would have to have the BitLocker password.
I then deleted the device from our local AD, from Intune, and also the Autopilot entry.
After some time I connected the device to wifi and just let it run. No one logged on. I assume that during this time it connects to Intune and syncs. I guess that’s when the decryption of the hard drive must happen.
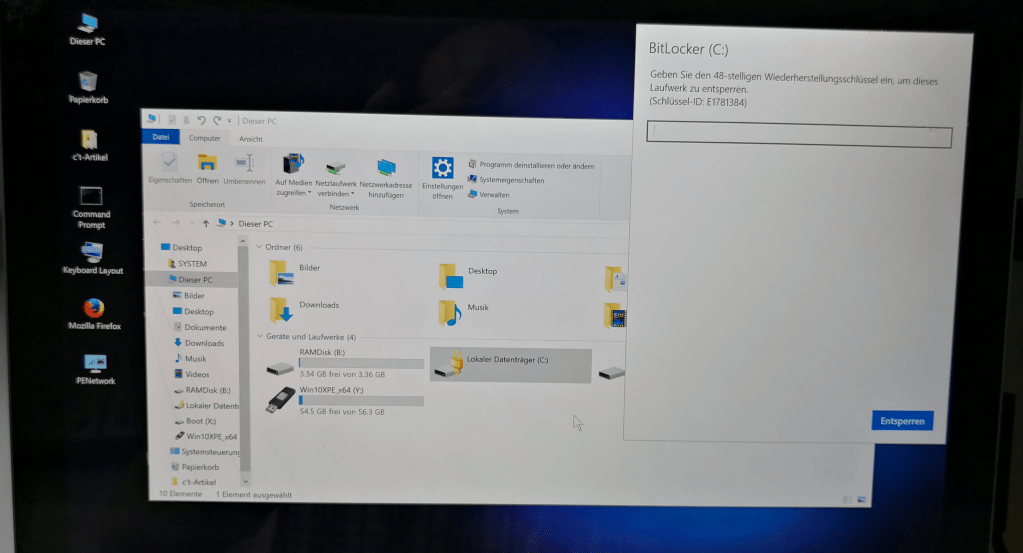
Anyway, after this wifi connection the hard disk is no longer encrypted. If you boot the device from a USB stick again, you can access all files on the hard disk.
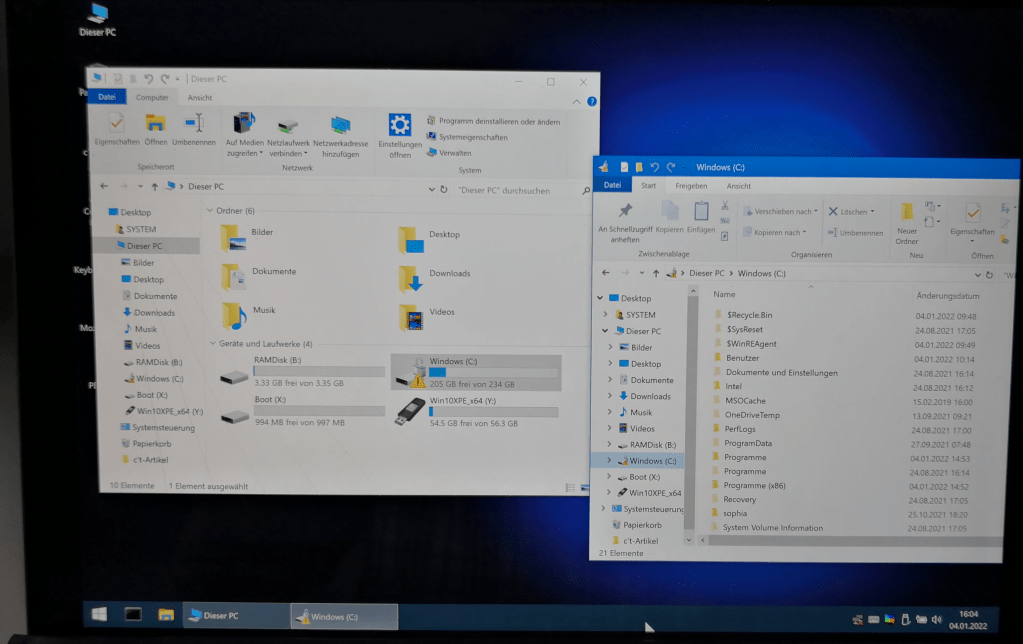
This is not at all the behavior that is desired. The hard disk should definitely remain encrypted for security reasons, even if the device is deleted from the admin portal.
The exclamation mark on the drive says that the drive is still encrypted but the protectors got suspended.
Suspending protectors can have many reasons and the main one is that the system got installed an update that needs a reboot.
Thanks for your answer.
That would be a bad behavior.So a thief could steal an encrypted device, wait until a new Windows update is available, connect the device to the Internet (without logging in, since he has no password) and wait until the device has installed the update. After that, he could boot from a USB stick and would have full access to the file system. Sounds like a bad solution to me.
Within your article we checked this also in our environment: same behavior. The drive is still encrypted but the protector is turned off when the object gets deleted in Intune.
Now we have an openened Microsoft Incident, the Engineer was surprised and will contact the product group.
Thanks. I’ve also opened a support case. Good to hear that you were able to reproduce the problem. So it seems that it is not just a configuration error on my side. But I’m still hoping that this is not by design and the product group will find a good solution.
Any solution from Product group ?
Only that this is by design. Looks like the problem are the byod devices. But a switch in Intune after pressing delete where you could choose if you would let the disk encrypted for company owned devices or not for private devices would address both scenarios.